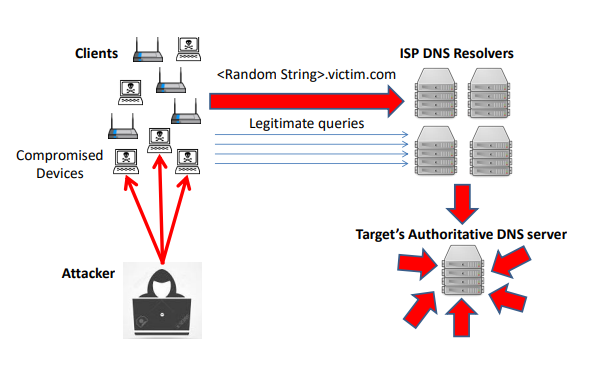
How To Detect Ddos Attack On Windows

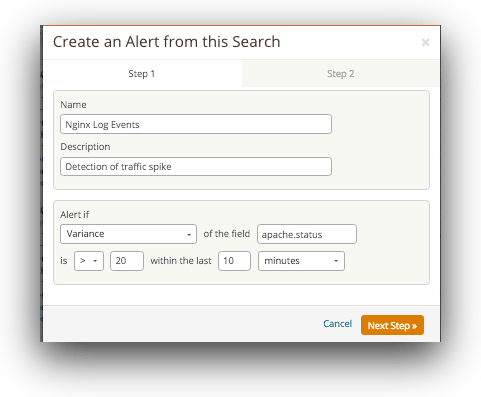
In the name field give your policy name and type a description.
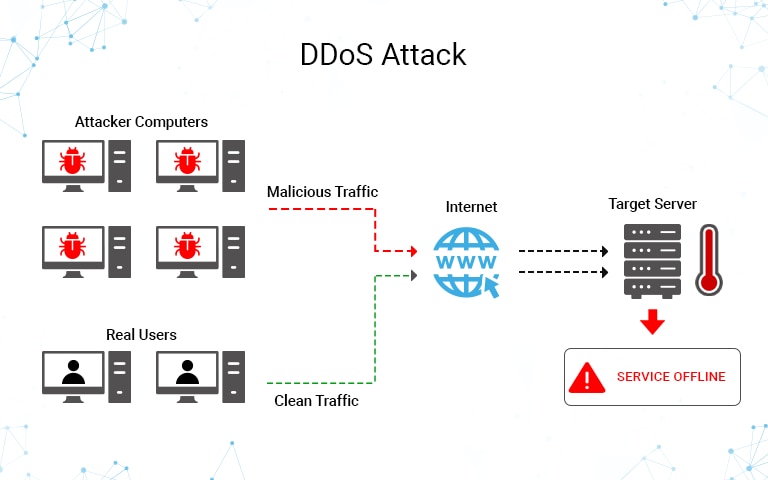
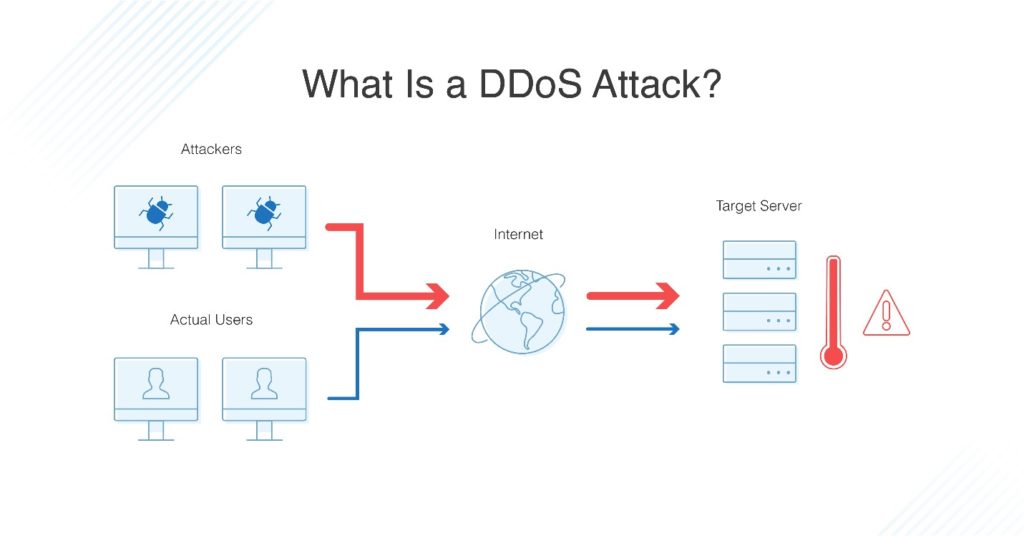
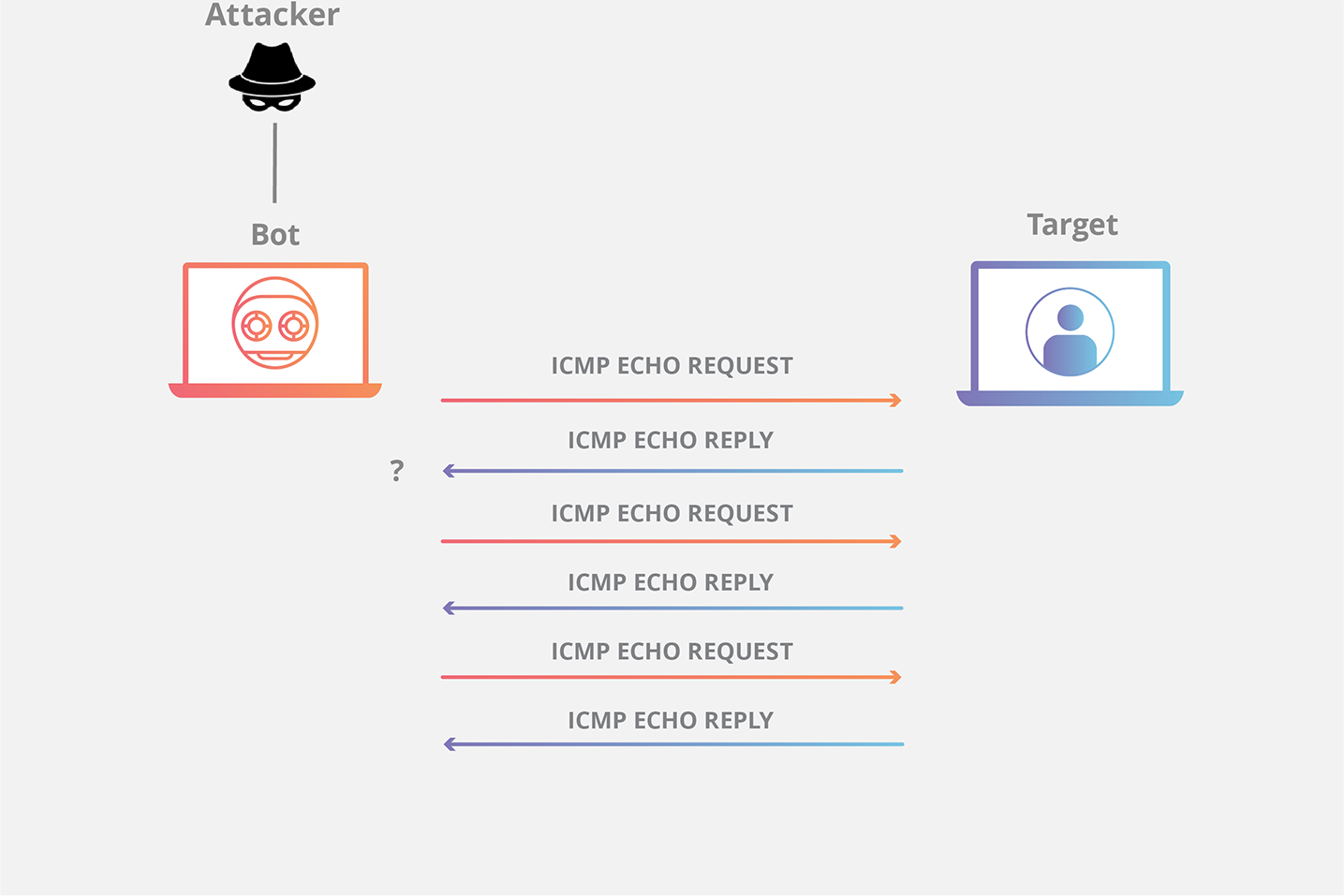
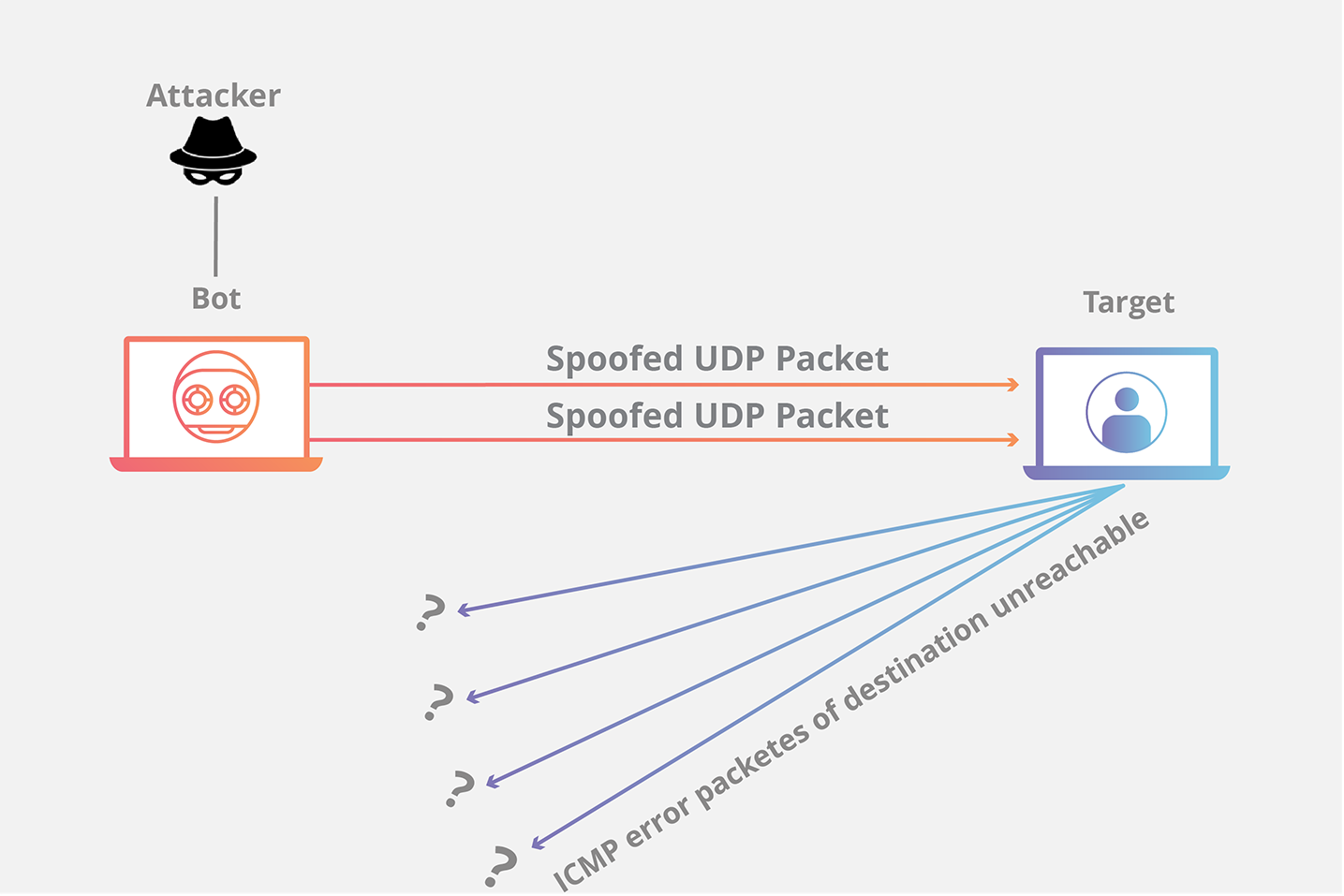
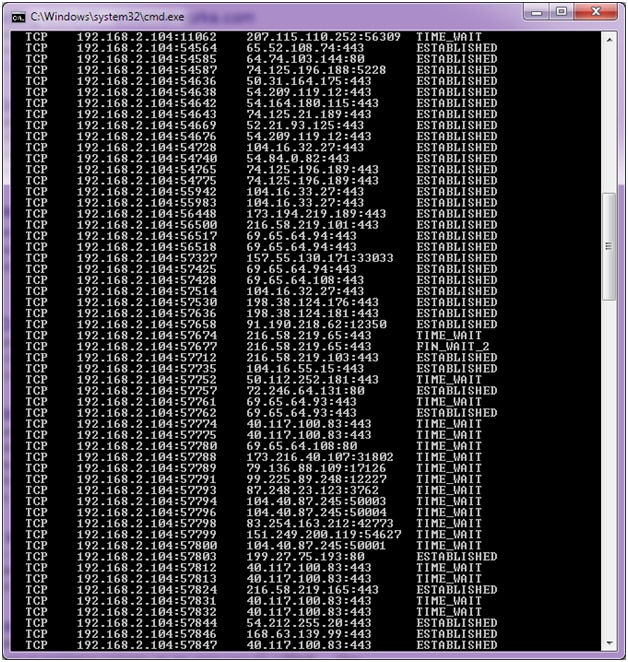
How to detect ddos attack on windows. Displays active tcp connections however addresses and port numbers are expressed numerically and no attempt is made to determine names. Even in the article you linked. This blog provides you an overview on how to identify ddos attack using netstat command. Can i block dos or ddos attack via windows firewall.
You can view this by logging into your account with your web host and opening cpanel. Ddos attacks are quick to start killing performance on the server. Now in the left side you will see ip security policies on local computer. Solarwinds sem is designed to detect exterior threats like ddos attacks by collecting normalizing and correlating logs from across your system to provide deeper visibility and more easily catch patterns that could signal an attack.
I love the windows firewall but don t agree it s a tool for preventing dos attacks. An ip address makes x requests over y seconds your server responds with a 503 due to service outages. There are several clues that indicate an ongoing ddos attack is happening. Netstat an grep 80 sort.
The most effective way to mitigate a ddos attack is to know when it s happening immediately when the attack begins. Display all active internet connections to the server and only established connections are included. Displays active tcp connections and includes the process id pid for each connection. Click start click run type secpol msc.
It usually starts intermittently displaying this error but heavy attacks lead to permanent 503 server responses for all of your users. With iis the server often returns a 503 service unavailable error. Scroll down to the logs section and select bandwidth. Best practices for preventing dos denial of service attacks the only mention of the word firewall is in the recommendation to use isa.
Show only active internet connections to the server on port 80 and sort the results. A normal bandwidth chart for the last 24 hours should show a relatively constant line with the exception of a few small spikes. However another sign of a ddos attack is a very strong spike in bandwidth. If a threat is detected sem can alert admins as well as deploy automatic responses to block activity and sever connections as needed.
Which is an application.